Formal Understanding Biometric Authentication
Fingerprints, facial, iris recognition, and handwritten signature
Biometrics is the most suitable means of identifying and authenticating individuals in a reliable and fast way through unique biological characteristics.
Biometric systems can be used in two distinct modes as follows:
- Verification (1-1): determining whether a person is who he claims to be.
- Identification (1-n): determining who the person is.
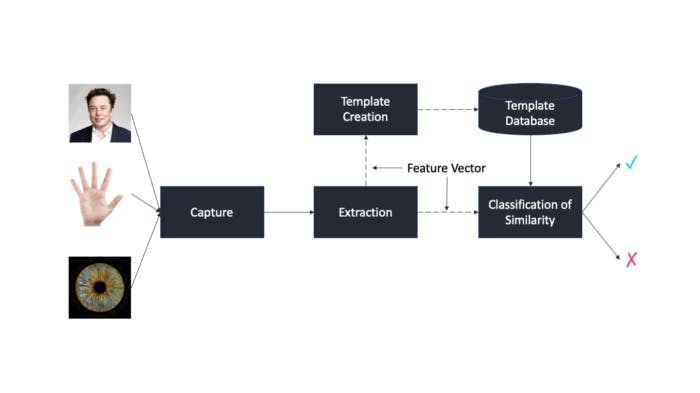
A biometric system operates by firstly acquiring biometric data from an individual, then extracting feature set from the data, and finally comparing the feature set with the template in the database as shown in the below figure.
History of Biometrics
In the second century B.C., the Chinese emperor Ts'In She was already authenticating specific seals with a fingerprint.
Fingerprints were first used in a commercial setting in 1858 by William James Herschel, a British administrator in India.
Having been put in charge of building roads in Bengal, he had his subcontractors sign contracts with their fingers.
That was an early form of biometric authentication and a sure way of finding them more quickly if they defaulted.
At the end of the 19th century, Bertillon, a French police officer, took the first steps in scientific policing.
He used body measurements taken of specific anatomical characteristics to identify reoffending criminals, which often proved successful.
It generally combines other security technologies such as smart ID cards and chips (for electronic passports).

Biometric authentication
Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance.
Biometric identification
Biometric identification consists of determining the identity of a person.
- The aim is to capture an item of biometric data from this person.
- This data is then compared to the biometric data of several other persons kept in a database.
Biometric Techniques
Biometric authentication techniques are classified by the type of characteristics evaluated: physiological attributes or behavioral singularities.
Physiological Biometrics
Physiological biometrics are based on classifying a person according to data obtained as part of the human body such as his fingerprints, face, or eye iris.
Fingerprint Recognition
The most popular biometric to date, fingerprint recognition, can utilize a number of approaches to classification, based on minutiae which are a reproduction of epidermal friction skin ridges found on the palm side of the fingers and thumbs, the palms, and soles of the feet.
- A fingerprint will remain unchanged during a lifetime.
- Fingerprints have general ridge patterns.
Hand Geometry
We use the geometric features of the hand such as the lengths of fingers and the width of the hand to identify an individual.
Facial Recognition
The system record face images through a digital video camera and then analyze facial characteristics like the distance between the eyes, nose, mouth, and jaw edges.
Iris Recognition
The iris is the colored tissue surrounding the pupil of the eye and is composed of intricate patterns with many furrows and ridges.
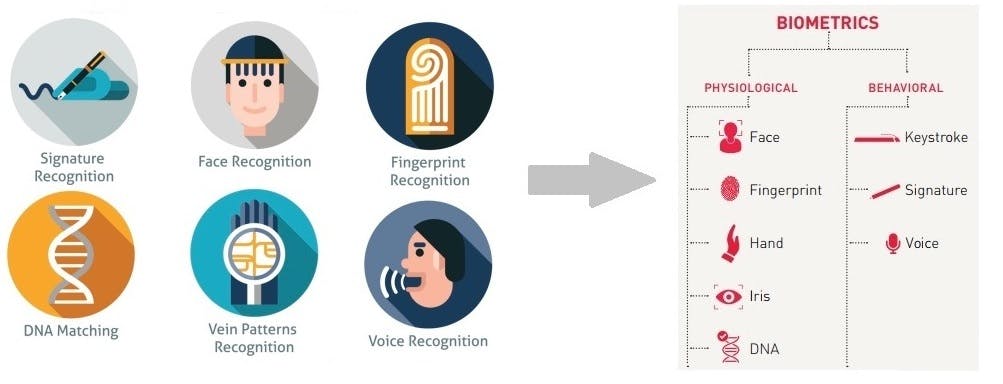
Behavioral Biometrics
The most common are:
- voice recognition
- signature dynamics (speed of movement of pen, accelerations, pressure exerted, inclination)
- keystroke dynamics
- the way we use objects
- gait, the sound of steps
- gestures.
The different techniques used are the subject of ongoing research and development and are being improved continuously.
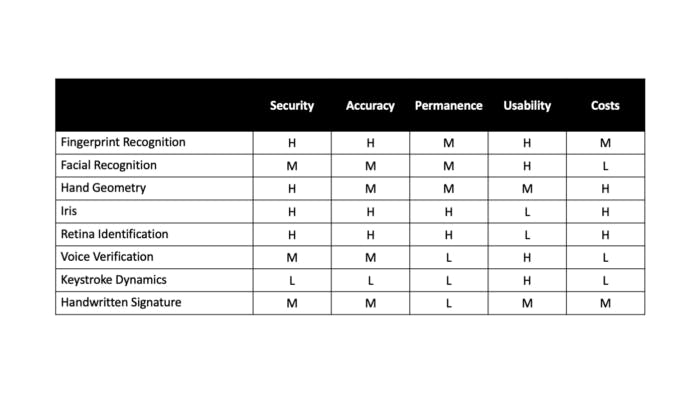
Comparison of biometric authentication methods
We compare biometric authentication methods based on the following six characteristics are security, accuracy, permanence, usability, adequacy, and costs with 3 levels which are high, medium, and low.
Biometrics hacking?
Replay attacks
In a replay attack, an intruder has been able to record successful login sessions involving biometric systems or devices and later tries to perform authentication on his own by replaying the captured data.
Faked credentials
Some biometric systems may be vulnerable to attacks using fake credentials. For example, if a biometric system relies on facial recognition a hacker may be able to fool such a system by holding a life-size photograph of the user in front of the camera.
Stolen credentials
Some biometric systems are more vulnerable to stolen credential attacks than others. But the thought of a stolen eye is just gruesome to us.

Biometrics Trends
Faced with document fraud and identity theft, terrorism and cybercrime, international regulation changes, new biometric security solutions are being implemented.
Biometrics can be defined as the most practical means of identifying and authenticating individuals in a reliable and fast way through unique biological characteristics.
Of course, increased public acceptance, massive accuracy gains, a rich offer, and falling prices of sensors, IP cameras, and software make it all the easier to install biometric systems.

Sources

